Encrypting communications in Elasticsearch
This article provides steps to configure SSL security for Elasticsearch. Elasticsearch by default doesn't have encrypted communication between Nodes or other external sources interacting.We can enable the Encrypted communication between nodes and other external components.
We require are cluster to go ahead with Encryption of Elasticsearch communications, if you have not already setup one please refer Elasticsearch High Availability Production Cluster Setup
Current Configuration is done using Elasticseach 7.4.0 version.
Let dive into configuration.
Before we start we should be having minimum of two master nodes and one data node in cluster to start.
1. Generate Certificates: Elasticsearch provides utility to generate self signed certificates. "elasticsearch-certutil" is the utility which could be found in "bin" directory of elasticsearch directory.
ENTER
ENTER
bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
ENTER
ENTER
ENTER
The above commands with Enter\Specified inputs generate two files "elastic-certificates.p12", "elastic-stack-ca.p12" under Elasticsearch base directory which could be used by all the nodes of the cluster.
Place certificates under "config" folder of all the nodes the cluster.
CA certificate generated by other providers Certificate authority could be used to instead of self signed certificates.
2. Nodes SSL Communication Configuration: Under "config" folder you will find "elasticsearch.yml" which is where configuration is done. Add the below at bottom along with the current cluster configuration.
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
Once configuration change are made to all the nodes in the cluster, restart the all nodes. This will create Encrypted communication between all the nodes in cluster. Now you will not be able to check the nodes in cluster until built-in users are configured with password.
3. Configure built-in user’s passwords: Once the clusters are configured with SSL communication, need to configure password for built-in users to access the details of nodes in cluster. Elasticsearch has provided "elasticsearch-setup-passwords" utility with which we can setup the passwords.
Note: Once passwords are set for the cluster the utility will not work again.
Below are two modes in which you can create passwords of which one needs to picked depending on requirements, there are more ways apart from below please refer to documentation.
Users for which password need to be created: elastic, kibana, logstash_system, beats_system, apm_system, and remote_monitoring_user users
- Interactive Mode: This mode allows user to create user defined password of their choice
bin/elasticsearch-setup-passwords interactive
- Randomly-generated passwords: This mode generates random password for all the users and printed to console.
bin/elasticsearch-setup-passwords auto
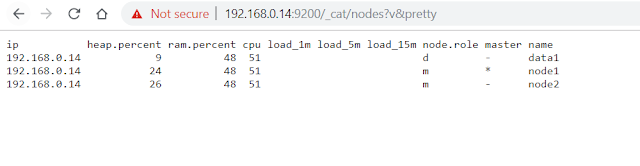
Once we are done with password creation we can now access the node details using the regular url, but you would be prompted for user id and password. Please enter elastic user as user name and password as set which will then display nodes information.
4. Configure SSL for external communications: : Lets add more configuration to "elasticsearch.yml" under "config" to enable SSL for communication with external sources.
Note: Built-in user password should be created before this step.
Add the below at bottom along with the current configuration.
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.keystore.path: elastic-certificates.p12
xpack.security.http.ssl.truststore.path: elastic-certificates.p12
xpack.security.http.ssl.client_authentication: optional
Validate the nodes using SSL url. Please use https in the url else elasticsearch will not process the request.
Once all the above configuration change are made to all the nodes in the cluster, restart the all nodes. This will create Encrypted communication between all the nodes in cluster and enable SSL configuration for external sources.
All the configuration files are available at GitHub.